SAVE PASS 보안정책
Savepass.net 은 아래와 같은 보안정책을 운영하고 있습니다.
1. HTTPS 보안통신
웹주소에 https:// 를 사용하는 것에서 알 수 있듯이, 사용자의 컴퓨터와 웹서버 사이의 데이터 전달과장에 보안통신을 사용하므로, 웹사이트 상에서의 활동을 추적하거나 정보를 도용할 수 없습니다.
2. 로그인 정보 암호화
로그인에 사용되는 비밀번호는 복호화 할 수 없는 해시 함수로 일방향 암호화하여 데이터베이스에 저장합니다.
복호화 할 수 없는 일방향 암호화이므로, 로그인을 위해 아이디와 비번을 입력할 때에 암호화된 정보끼리 비교함으로써 로그인 정보를 확인할 수 있을 뿐, 비밀번호가 무엇인지는 데이터베이스가 탈취되는 사고가 발생하여도 탈취자가 확인할 수 없습니다.
3. 사용자 입력정보 암호화
Savepass.net 에 기록하는 아이디 및 비번은 한국인터넷 진흥원에서 배포한 ‘SEED 블록 알고리즘’에 따라 암호화 되어 저장됩니다.
암호화 알고리즘 자체는 공개된 것이나, 암호화 과정에서 사용되는 KEY가 없이는 복호화 할 수 없으므로, 데이터베이스가 탈취되는 사고가 발생하여도 탈취자가 확인할 수 없습니다.
4. 미완성 데이터 기록 권장
비록 모든 정보가 암호화되어 저장되지만, 비밀번호 정보는 중요한 정보이므로, 기록할 때에도 정확한 내용을 기록하기 보다 자기자신만 확인할 수 있는 수준으로 미완성 데이터 형태로 기록하실 것을 권장합니다.
예를 들어, 비밀번호가 abcd1234 이라면, a***1*** 와 같이 기록하여 활용함으로써 본인은 이 정보만으로도 알 수 있으나, 다른 사람은 비록 정보가 유출되더라도 쉽게 알 수 없도록 하시길 바랍니다.
HTTPS의 정의
HTTPS (HyperText Transfer Protocol Secure)
HTTP에 데이터 암호화(Secure Socket)가 추가된 프로토콜로서,
인터넷 상에서 정보를 암호화하는 SSL 프로토콜을 사용하여 클라이언트와 서버가 자원을 주고 받을 때 사용하는 통신 규약입니다.
HTTPS를 사용하여 전송되는 데이터의 보안은 다음과 같은 3중 핵심 보호층을 제공하는 전송 계층 보안 프로토콜(TLS)을 통해 더욱 강화됩니다.
암호화 : 교환되는 데이터를 암호화하여 침입자로부터 보호합니다. 즉, 사용자가 웹사이트를 탐색하는 동안 아무도 대화를 ‘엿들을’ 수 없고 페이지에서 활동을 추적할 수 없으며 정보를 도용할 수 없습니다.
데이터 무결성 : 데이터가 전송되는 동안 의도적이든 그렇지 않든 모르는 사이에 데이터가 변경되거나 손상되는 일을 방지합니다.
인증 : 사용자가 의도된 웹사이트와 통신 중임을 입증합니다. 중간자 공격을 차단하고 사용자의 신뢰를 구축하게 되어 다른 비즈니스 이점으로 이어지게 됩니다.
HTTPS 통신 흐름
공개키 암호화 방식을 SSL통신 절차에 적용을 하면 흐름은 다음과 같습니다.
-
클라이언트는 서버에 접속하면, 서버인증서(CA)를 받는다.
-
서버인증서 신뢰 여부 체크 후, 공개키를 추출한다.
-
클라이언트는 서버와 통신하는 동안만 사용할 대칭키를 임의로 만들고, 해당 대칭키를 공개키로 암호화 후 전송 한다.
-
서버는 개인키로 클라이언트가 보낸 메시지를 복호화하여 대칭키를 추출하고, 해당 대칭키를 이용하여 클라이언트와 통신한다.
출처
https://en.wikipedia.org/wiki/HTTPS
https://developers.google.com/search/docs/advanced/security/https?hl=ko
암호기술의 정의
암호기술은 중요한 정보를 읽기 어려운 값으로 변환하여 제 3자가 볼 수 없도록 하는 기술입니다. 암호기술의 안전성은 수학적인 원리에 기반하며, 보안에 있어서 중요한 정보를 직접적으로 보호하는 원천기술 입니다.
암호기술을 통해 보호하고자 하는 원본 데이터를 평문(plaintext)라고 하며, 평문에 암호기술을 적용한 것을 암호문(ciphertext)라고 합니다. 이렇게, 평문에 암호기술을 적용하여 암호문으로 변환하는 과정을 암호화라고 하며, 다시 평문으로 복원하는 과정을 복호화라고 합니다. 암호화하기 위해서는 암호 키(key)가 필요하며, 키가 있어야만 암호문을 복호화할 수 있습니다. 그렇게 때문에 암호 키는 비밀(secret)로 유지되어야 하며 제3자가 알 수 없어야 합니다.
암호기술을 이용하여 데이터 기밀성, 데이터 무결성, 인증 및 부인 방지 등의 기능을 제공할 수 있습니다.
기밀성 : 허락되지 않은 사용자 또는 객체가 정보의 내용을 알 수 없도록 하는 성질
무결성 : 허락되지 않은 사용자 또는 객체가 정보를 함부로 수정할 수 없도록 하는 성질
인증 : 사용자 또는 객체의 디지털 정체성을 식별
부인방지 : 정보를 보낸 사람이 나중에 정보를 보냈다는 것을 부인하지 못하도록 함
암호기술의 종류
1. 대칭키 암호
대칭키 암호(Symmetric-key Cryptography)는 암ㆍ복호화에 같은 암호 키를 사용하는 알고리즘이며, 송신자와 수신자는 암호 키가 노출되지 않도록 비밀로 관리해야 합니다. 대칭키 암호는 내부 구조가 간단한 치환과 전치의 조합으로 되어 있어 연산 속도가 빠르다는 장점이 있습니다. 하지만, 송ㆍ수신자 간에 동일한 키를 공유해야 하므로 많은 사람들과의 정보 교환 시 많은 키를 관리해야 하는 어려움이 있습니다.
(1) 블록 암호
블록 암호(Block Cipher)는 평문을 고정된 크기의 블록단위로 암ㆍ복호화를 수행하며, 각 블록마다 동일한 키가 사용됩니다. 블록 암호는 고정된 크기로 평문을 나누기 때문에, 원하는 길이를 맞추기 위하여 패딩(padding)이라는 기법을 이용합니다. 또한, 하나의 키로 여러 블록을 안전하게 처리하기 위하여 운용 방식(mode of operation)이라는 절차를 이용합니다.
Shannon의 암호 이론에 의하면 전치와 환자를 반복시켜 평문의 통계적 성질이나 암호 키와의 관계가 나타나지 않아 안전한 암호를 구성할 수 있습니다. 대표적인 블록 암호 알고리즘으로는 국산 알고리즘인 SEED, HIGHT, ARIA, LEA와 외산 알고리즘인 DES, AES 등이 있습니다.
(2) 스트림 암호
스트림 암호(Stream Cipher)는 평문과 동일한 길이의 키스트림(key stream) 수열을 생성하여, 평문과의 XOR연산을 통하여 암ㆍ복호화를 수행합니다. 키스트림 수열을 생성할 때, 평문과 독립적으로 생성하는 경우를 동기식 스트림 암호라고 하며, 반대로 평문이 키스트림 수열에 영향을 미치는 경우를 비동기식(혹은 자기동기) 스트림 암호라고 합니다. 구현 여건이 제약되는 환경에서 구현이 용이하며, 무선 통신 등의 환경에 주로 사용된다. 대표적인 스트림 암호 알고리즘으로 RC4, A5/1, A5/2 등이 있습니다.
2. 비대칭키 암호
(1) 공개키 암호
비대칭키 암호는 공개키 암호(Public-key Encryption)라고도 하며, 대칭키 암호와 달리 암·복호화에 서로 다른 키를 사용하는 알고리즘입니다. 송신자는 수신자의 공개키를 이용하여 암호화하며, 수신자는 자신의 공개키로 암호화된 암호문을 자신의 개인키로 복호화할 수 있습니다. 공개키 암호는 수학적인 난제를 기반으로 설계되어 있고 암복호화에 복잡한 수학 연산을 사용하기 때문에, 대칭키 암호에 비해 효율성이 떨어질 수 있습니다. 하지만, 여러 송신자가 하나의 공개키로 암호화를 수행하기 때문에 사용자가 많더라도 키를 관리하는 데에 유리합니다. 대표적인 알고리즘으로 RSA, ElGamal, ECC 등이 있습니다.
(2) 전자 서명
전자 서명(Digital Signature)은 인터넷 상에서 본인임을 증명하기 위해 서명을 하는 수단으로, 공개키 암호를 거꾸로 활용하는 방식입니다. 송·수신자의 역할이 반대로 되어, 개인키를 소유한 사람만이 전자 서명 알고리즘을 통해 평문에 대한 서명 값을 생성할 수 있습니다. 생성된 서명 값에 대하여 공개키를 이용하면 평문을 검증할 수 있기 때문에, 누구나 그 서명을 검증할 수 있게 됩니다. 대표적인 전자 서명 알고리즘으로 DSA, RSA SIgnature, ECDSA 등이 있습니다.
3. 해시 함수
해시 함수(Hash Function)는 임의의 길이의 메시지를 입력으로 받아 고정된 길이의 해시 값을 출력하는 함수입니다. 해시 함수에는 암호 키가 사용되지 않기 때문에, 같은 입력에 대해서 항상 같은 해시 값을 얻을 수 있습니다. 이러한 성질로 인해 입력 메시지에 대한 변경할 수 없는 증거 값을 만들어냄으로서, 주로 무결성을 제공하는 목적으로 사용됩니다.
안전한 해시 함수는 역상 저항성, 제 2 역상 저항성, 충돌 저항성을 가져야 합니다.
– 역상 저항성 : 어떤 해시 값에 대하여, 원래 입력 값을 찾는 것이 어려워야 하며, 이를 일방향성(One-wayness)이라고도 합니다.
– 제 2 역상 저항성 : 입력 값에 대하여, 그 입력값의 해시 값과 같은 해시 값을 같은 또다른 입력값을 찾는 것이 어려워야 합니다.
– 충돌 저항성 : 같은 해시 값을 갖는 두 입력 값을 찾는 것이 어려워야 합니다.
해시 함수는 데이터가 통신 중 변조되지 않았다는 무결성 검증이 필요할 때, 메시지인증코드(MAC, Message Authentication Code)의 형태로 사용될 수 있습니다. 또한, 해시 함수는 전자서명에도 활용될 수 있습니다. 전체 메시지가 아닌 짧은 해시 값에 전자 서명을 계산하면 효율적으로 서명 값을 생성할 수 있습니다. 원래 메시지가 아닌 해시 값에 대해 서명을 하였지만 같은 해시 값을 갖는 다른 메시지를 찾는 것이 어렵기 때문에, 이 서명은 메시지에 대한 서명이라고 인정됩니다. 대표적인 해시 함수로는 MD5, HAS-160, SHA-1, SHA-2, SHA-3 등이 있습니다.
출처 : KISA 암호이용활성화 – 암호기술의 정의. https://seed.kisa.or.kr/kisa/intro/EgovDefinition.do.
SEED 란?
1. 개요
SEED는 전자상거래, 금융, 무선통신 등에서 전송되는 중요 정보를 보호하기 위해 1999년 2월 한국정보보호진흥원을 중심으로 국내 암호 전문가들이 참여하여 순수 국내기술로 개발한 블록암호 알고리즘으로, 2005년에는 국제 표준화 기구인 ISO/IEC 국제 블록암호알고리즘 IETF표준으로 제정되었습니다.
2. 블록암호 알고리즘
SEED는 128비트의 암⋅복호화키를 이용하여 임의의 길이를 갖는 입력 메시지를 128비트의 블록단위로 처리하는 128비트 블록암호 알고리즘입니다. 따라서 임의의 길이를 가지는 평문 메시지를 128비트씩 블록단위로 나누어 암호화하여 암호문을 생성합니다 .
3. 운영모드
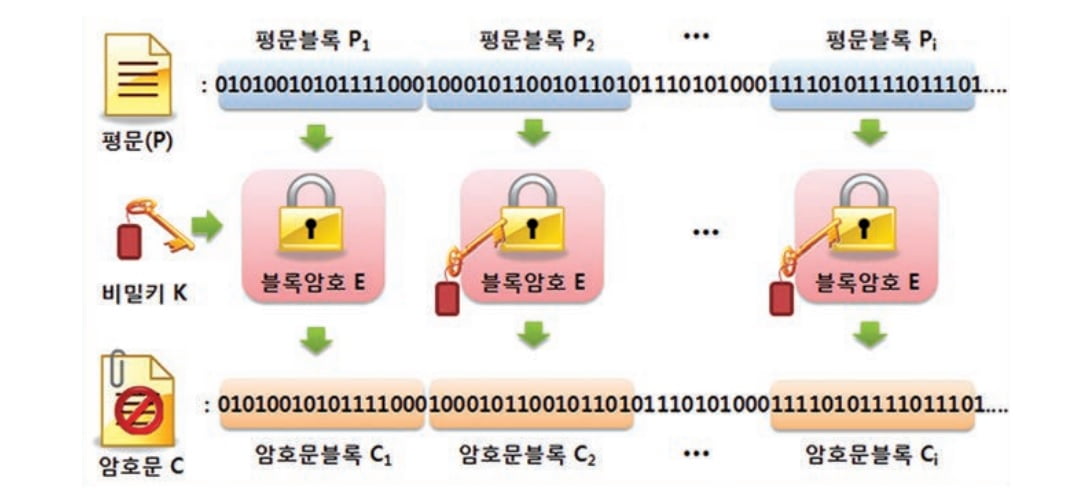
운영모드란, 여러 개의 입력 블록들을 블록암호에 적용하여 암⋅복호화하는 방법에 대한 정의입니다. 이러한 운영모드는 블록암호와는 독립적으로 정의되는데, 대표적으로 가장 널리 이용되는 블록암호의 기밀성 운영모드에는 ECB(Electronic Code Book) 모드, CBC(Cipher Block Chaining) 모드, CFB(Ciphertext FeedBack) 모드, OFB(Output FeedBack) 모드, CTR(CounTeR) 모드, 인증 운영 모드에는 CMAC(Cipher-based MAC) 모드, 인증 암호화 운영모드에는 CCM(Counter with CBC-MAC) 모드, GCM(Galois/Counter Mode) 모드가 있습니다. 아래 그림은 ECB 모드에 따른 암호화 과정을 정리한 것입니다.
4. SEED 보급
SEED 는 전자상거래, e-mail, 인터넷 뱅킹, 데이터 저장, VPN, 지적재산권 보호 등의 다양한 분야에서 사용되고 있으며, 2009년 5월 말까지 nCipher, RSA Security 등의 국외 정보보호업체를 포함하여 3232개 이상의 국내외 기업 및 학교에 SEED 소스코드가 e-mail을 통해 배포되었으며, 아래 주소에서 샘플을 다운로드 받을 수 있습니다.
https://seed.kisa.or.kr/kisa/Board/17/detailView.do
5. SEED 암호화 테스트
한국인터넷진흥원 암호이용활성화 (https://seed.kisa.or.kr) 사이트에서 리눅스 환경에서 PHP 언어를 사용하는 웹서버용 모듈을 테스트 해 보실 수 있도록, CBC 운영모드와 ECB 운영모드로 구현된 SEED 암호화 모듈을 아래 위치에 설치하였습니다.
CBC 운영모드 테스트 : https://savepass.net/kisa/CBC
ECB 운영모드 테스트 : https://savepass.net/kisa/ECB
KISA 사이트에서 다운로드 받을 수 있으나, CBC 운영모드에 대한 테스트용 모듈은 아래와 같습니다.
<?php
require_once (‘KISA_SEED_CBC.php‘);
$g_bszUser_key = null;
if(isset($_POST[‘KEY’]))
$g_bszUser_key = $_POST[‘KEY’];
if($g_bszUser_key == null)
{
$g_bszUser_key = “88,E3,4F,8F,08,17,79,F1,E9,F3,94,37,0A,D4,05,89″;
}
$g_bszIV = null;
if(isset($_POST[‘IV’]))
$g_bszIV = $_POST[‘IV’];
if($g_bszIV == null)
{
$g_bszIV = “26,8D,66,A7,35,A8,1A,81,6F,BA,D9,FA,36,16,25,01″;
}
function encrypt($bszIV, $bszUser_key, $str) {
$planBytes = explode(“,“,$str);
$keyBytes = explode(“,“,$bszUser_key);
$IVBytes = explode(“,“,$bszIV);
for($i = 0; $i < 16; $i++)
{
$keyBytes[$i] = hexdec($keyBytes[$i]);
$IVBytes[$i] = hexdec($IVBytes[$i]);
}
for ($i = 0; $i < count($planBytes); $i++) {
$planBytes[$i] = hexdec($planBytes[$i]);
}
if (count($planBytes) == 0) {
return $str;
}
$ret = null;
$bszChiperText = null;
$pdwRoundKey = array_pad(array(),32,0);
//방법 1
$bszChiperText = KISA_SEED_CBC::SEED_CBC_Encrypt($keyBytes, $IVBytes, $planBytes, 0, count($planBytes));
$r = count($bszChiperText);
for($i=0;$i< $r;$i++) {
$ret .= sprintf(“%02X”, $bszChiperText[$i]).“,”;
}
return substr($ret,0,strlen($ret)-1);
/*
// 방법 2
$info = new KISA_SEED_INFO();
$message_length = count($planBytes);
KISA_SEED_CBC::SEED_CBC_init( $info, KISA_ENC_DEC::KISA_ENCRYPT, $keyBytes, $IVBytes );
$process_blockLeng = 32;
$outbuf = array_pad(array(), $process_blockLeng/4, 0);
for($i = 0; $i < $message_length-$process_blockLeng; )
{
Common::arraycopy_system($planBytes, $i, $pbszPlainText, 0, $process_blockLeng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszPlainText, $process_blockLeng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $process_blockLeng, $outbuf, $nRetOutLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC($outbuf, $nRetOutLeng);
Common::arraycopy_system($cdata, 0, $pbszCipherText, $i, $nRetOutLeng );
$i+= $nRetOutLeng;
}
$remainleng = $message_length%$process_blockLeng;
if($remainleng==0)
{
$remainleng = $process_blockLeng;
}
Common::arraycopy_system($planBytes, $i, $pbszPlainText, 0, $remainleng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszPlainText, $remainleng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $remainleng, $outbuf, $nRetOutLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC($outbuf, $nRetOutLeng);
Common::arraycopy_system($cdata, 0, $pbszCipherText, $i, $nRetOutLeng );
$i+= $nRetOutLeng;
KISA_SEED_CBC::SEED_CBC_Close( $info, $outbuf, 0, $nPaddingLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC($outbuf, $nPaddingLeng);
Common::arraycopy_system($cdata, 0, $pbszCipherText, $i, $nPaddingLeng );
$data = null;
$cdata = null;
$outbuf = null;
for($i=0;$i< sizeof($pbszCipherText);$i++) {
$ret .= sprintf(“%02X”, $pbszCipherText[$i]).”,”;
}
return substr($ret,0,strlen($ret)-1);
*/
}
function decrypt($bszIV, $bszUser_key, $str) {
$planBytes = explode(“,“,$str);
$keyBytes = explode(“,“,$bszUser_key);
$IVBytes = explode(“,“,$bszIV);
for($i = 0; $i < 16; $i++)
{
$keyBytes[$i] = hexdec($keyBytes[$i]);
$IVBytes[$i] = hexdec($IVBytes[$i]);
}
for ($i = 0; $i < count($planBytes); $i++) {
$planBytes[$i] = hexdec($planBytes[$i]);
}
if (count($planBytes) == 0) {
return $str;
}
$pdwRoundKey = array_pad(array(),32,0);
$bszPlainText = null;
// 방법 1
$bszPlainText = KISA_SEED_CBC::SEED_CBC_Decrypt($keyBytes, $IVBytes, $planBytes, 0, count($planBytes));
for($i=0;$i< sizeof($bszPlainText);$i++) {
$planBytresMessage .= sprintf(“%02X”, $bszPlainText[$i]).“,”;
}
return substr($planBytresMessage,0,strlen($planBytresMessage)-1);
/*
// 방법 2
$info = new KISA_SEED_INFO();
$nCipherTextLen = count($pbszCipherText);
$EncryptedMessage_length = count($planBytes);
if($EncryptedMessage_length%KISA_SEED_CBC::BLOCK_SIZE_SEED)
{
return “”;
}
KISA_SEED_CBC::SEED_CBC_init( $info, KISA_ENC_DEC::KISA_DECRYPT, $keyBytes, $IVBytes );
$process_blockLeng = 32;
$outbuf = array_pad(array(), $process_blockLeng/4, 0);
for($i = 0; $i < $EncryptedMessage_length-$process_blockLeng; )
{
Common::arraycopy_system($planBytes, $i, $pbszCipherText, 0, $process_blockLeng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszCipherText,$process_blockLeng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $process_blockLeng, $outbuf, $nRetOutLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC( $outbuf, $nRetOutLeng );
Common::arraycopy_system($cdata, 0, $pbszPlainText, $i, $nRetOutLeng );
$i+= $nRetOutLeng;
}
$remainleng = $EncryptedMessage_length%$process_blockLeng;
if($remainleng==0)
{
$remainleng = $process_blockLeng;
}
Common::arraycopy_system($planBytes, $i, $pbszCipherText, 0, $remainleng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszCipherText,$remainleng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $remainleng, $outbuf, $nRetOutLeng );
if(KISA_SEED_CBC::SEED_CBC_Close( $info, $outbuf, $nRetOutLeng, $nPaddingLeng))
{
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC( $outbuf, $remainleng-$nPaddingLeng );
Common::arraycopy_system($cdata, 0, $pbszPlainText, $i, $remainleng-$nPaddingLeng );
$message_length = $i+ $remainleng -$nPaddingLeng;
$result = array_pad(array(), $message_length, 0);
Common::arraycopy_system($pbszPlainText, 0, $result, 0, $message_length);
$data = null;
$cdata = null;
$outbuf = null;
for($i=0;$i< sizeof($result);$i++) {
$planBytresMessage .= sprintf(“%02X”, $result[$i]).”,”;
}
return substr($planBytresMessage,0,strlen($planBytresMessage)-1);
}
return “”;
*/
}
$enc = null;
$dec = null;
if(isset($_POST[‘ENC’]))
$enc = $_POST[‘ENC’];
if(isset($_POST[‘DEC’]))
$dec = $_POST[‘DEC’];
if($enc==null) {
$enc2 = “”;
} else {
//암호화 시작
$g_bszPlainText = $enc;
$enc2 = encrypt($g_bszIV, $g_bszUser_key, $g_bszPlainText);
}
if($dec==null) {
$dec2 = “”;
} else {
//복호화 시작
$g_bszChiperText = $dec;
$dec2 = decrypt($g_bszIV, $g_bszUser_key, $g_bszChiperText);
}
?>
<html>
<head>
<meta http-equiv=“Content-Type” content=“text/html; charset=utf-8”>
<title>국산암호 [SEED – CBC] 테스트 페이지</title>
</head>
<body>
<center>
<h1>국산 암호 [SEED-CBC] 테스트 페이지</h1>
<form name=“myform“ method=“post” action=“./index.php“>
<input type=“hidden” name=“method” id=“method” />
<table border=“0”>
<tr>
<td style=“text-align:center;”>
<form method=“post” action=“./index.php“>
<table border=“0”>
<tr><td></td><td><암호화 예제></td></tr>
<tr>
<td>키(KEY) : </td>
<td><textarea name=“KEY” style=“width:400px;height:100px;”><?=$g_bszUser_key?></textarea></td>
</tr>
<tr>
<td>초기값(IV) : </td>
<td><textarea name=“IV” style=“width:400px;height:100px;”><?=$g_bszIV?></textarea></td>
</tr>
<tr>
<td>평문 : </td>
<td><textarea name=“ENC” style=“width:400px;height:100px;”><?=$enc?></textarea></td>
</tr>
<tr>
<td></td>
<td><input type=“submit” name=“gogo“ value=“▼ 암호화“> </td>
</tr>
<tr>
<td>암호문 : </td>
<td><textarea name=“ENC2” style=“width:400px;height:100px;”><?=$enc2?></textarea></td>
</tr>
</table>
</form>
</td>
<td style=“width:1px;background-color:#aaaaff;”>
</td>
<td style=“text-align:center;”>
<form method=“post” action=“./index.php“>
<table border=“0”>
<tr><td></td><td><복호화 예제></td></tr>
<tr>
<td>키(KEY) : </td>
<td><textarea name=“KEY” style=“width:400px;height:100px;”><?=$g_bszUser_key?></textarea></td>
</tr>
<tr>
<td>초기값(IV) : </td>
<td><textarea name=“IV” style=“width:400px;height:100px;”><?=$g_bszIV?></textarea></td>
</tr>
<tr>
<td>암호문 : </td>
<td><textarea name=“DEC” style=“width:400px;height:100px;”><?=$dec?></textarea></td>
</tr>
<tr>
<td></td>
<td><input type=“submit” name=“gogo“ value=“▼ 복호화“></td>
</tr>
<tr>
<td>평문 : </td>
<td><textarea name=“DEC2” style=“width:400px;height:100px;”><?=$dec2?></textarea></td>
</tr>
</table>
</form>
</td>
</tr>
</table>
<div style=“margin-top:20px;margin-bottom:20px;”><font color=“#ff0000”>※ 평문 및 암호문은 Hex 값의 0x를 제외하고 콤마로 구분하여 띄어쓰기 없이 입력합니다.(ex : 00,01,0A,0B)</font></div>
<div style=“border: 1px solid #aaaaff; background-color:#ddddff;”>
<table border=“0”>
<tr>
<td><키(KEY)> : </td>
<td>88,E3,4F,8F,08,17,79,F1,E9,F3,94,37,0A,D4,05,89</td>
</tr>
<tr>
<td><초기값(IV)> : </td>
<td>26,8D,66,A7,35,A8,1A,81,6F,BA,D9,FA,36,16,25,01</td>
</tr>
<tr>
<td><평문> : </td>
<td>00,01,02,03,04,05,06,07,08,09,0A,0B,0C,0D,0E,0F</td>
</tr>
<tr>
<td><암호문> : </td>
<td>75,DD,A4,B0,65,FF,86,42,7D,44,8C,54,03,D3,5A,07,D3,5A,AB,86,7C,8B,F2,55,7D,82,38,8E,A7,C0,D0,F1</td>
</tr>
</table>
</div>
</form>
</center>
</body>
</html>
단, KISA 에서 제공하는 테스트 모듈은 프로그래머를 위한 것으로, 16진수로 변환된 값을 ‘평문’ 으로 입력해야 합니다. 이러한 번거로움을 덜고자 KISA 모듈을 조금 업데이트 해 보았습니다.
CBC 운영모드 테스트 : https://savepass.net/kisa/CBCGEN
통상 사용하는 글을 ‘평문’ 으로 넣어서 암호화 및 복호화 하는 과정을 테스트 할 수 있도록 수정해 보면 아래와 같습니다.
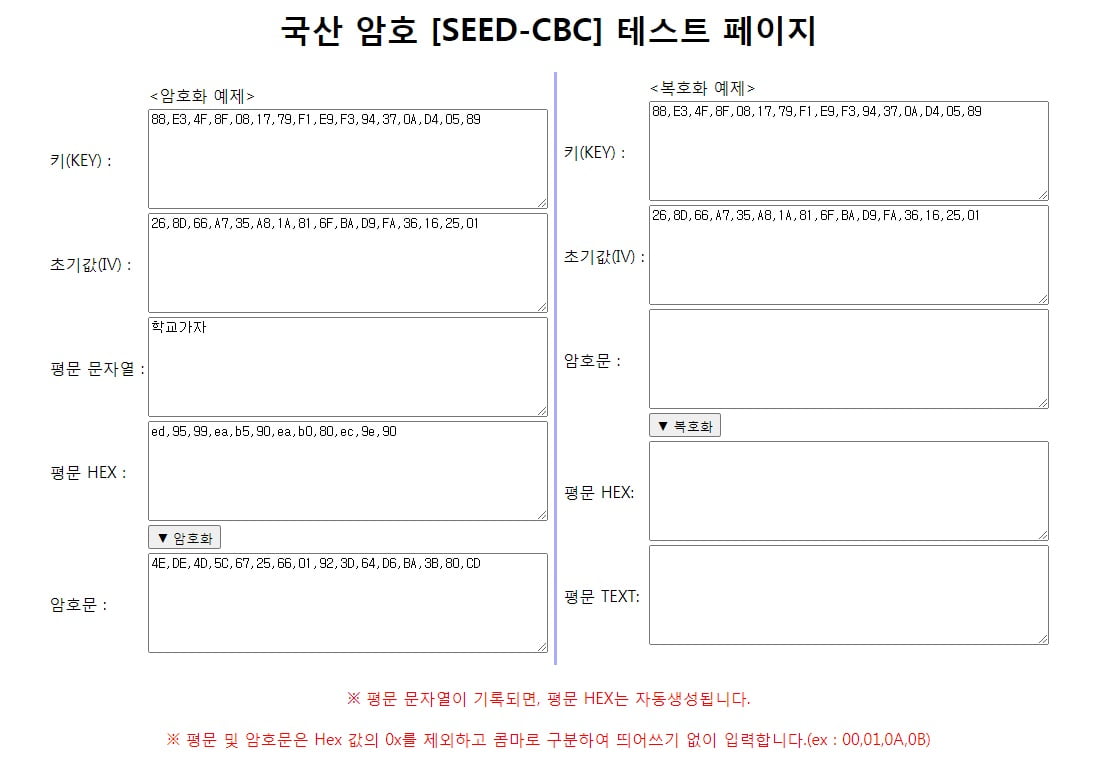

평문 ‘학교가자’ 를 암호화하면,
1) ‘학교가자’ 를 16진수 문자열 (평문 HEX) ‘ed,95,99,ea,b5,90,ea,b0,80,ec,9e,90’ 로 변환하고,
2) 이 평문HEX 값을 암호화 키값(KEY)과 암호화 초기값 (IV)를 조합하여 암호문 ‘4E,DE,4D,5C,67,25,66,01,92,3D,64,D6,BA,3B,80,CD’ 를 생성하게 됩니다.
암호문 ‘4E,DE,4D,5C,67,25,66,01,92,3D,64,D6,BA,3B,80,CD’ 을 복호화 하면,
1) 암호화 키값(KEY)과 암호화 초기값 (IV) 값을 활용하여 16진수 문자열 (평문HEX) 를 얻어내고,
2) 이를 보통의 문자열로 변환하면 ‘학교가자’로 환원됩니다.
이렇게 통상의 문자열로 테스트 할 수 있도록 수정된 테스트 모듈의 소스코드는 아래와 같습니다.
이렇게 통상의 문자열로 테스트 할 수 있도록 수정된 테스트 모듈의 소스코드는 아래와 같습니다.
<?php
require_once (‘KISA_SEED_CBC.php‘);
$g_bszUser_key = null;
if(isset($_POST[‘KEY’]))
$g_bszUser_key = $_POST[‘KEY’];
if($g_bszUser_key == null)
{
$g_bszUser_key = “88,E3,4F,8F,08,17,79,F1,E9,F3,94,37,0A,D4,05,89″;
}
$g_bszIV = null;
if(isset($_POST[‘IV’]))
$g_bszIV = $_POST[‘IV’];
if($g_bszIV == null)
{
$g_bszIV = “26,8D,66,A7,35,A8,1A,81,6F,BA,D9,FA,36,16,25,01″;
}
function encrypt($bszIV, $bszUser_key, $str) {
$planBytes = explode(“,“,$str);
$keyBytes = explode(“,“,$bszUser_key);
$IVBytes = explode(“,“,$bszIV);
for($i = 0; $i < 16; $i++)
{
$keyBytes[$i] = hexdec($keyBytes[$i]);
$IVBytes[$i] = hexdec($IVBytes[$i]);
}
for ($i = 0; $i < count($planBytes); $i++) {
$planBytes[$i] = hexdec($planBytes[$i]);
}
if (count($planBytes) == 0) {
return $str;
}
$ret = null;
$bszChiperText = null;
$pdwRoundKey = array_pad(array(),32,0);
//방법 1
$bszChiperText = KISA_SEED_CBC::SEED_CBC_Encrypt($keyBytes, $IVBytes, $planBytes, 0, count($planBytes));
$r = count($bszChiperText);
for($i=0;$i< $r;$i++) {
$ret .= sprintf(“%02X”, $bszChiperText[$i]).“,”;
}
return substr($ret,0,strlen($ret)-1);
/*
// 방법 2
$info = new KISA_SEED_INFO();
$message_length = count($planBytes);
KISA_SEED_CBC::SEED_CBC_init( $info, KISA_ENC_DEC::KISA_ENCRYPT, $keyBytes, $IVBytes );
$process_blockLeng = 32;
$outbuf = array_pad(array(), $process_blockLeng/4, 0);
for($i = 0; $i < $message_length-$process_blockLeng; )
{
Common::arraycopy_system($planBytes, $i, $pbszPlainText, 0, $process_blockLeng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszPlainText, $process_blockLeng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $process_blockLeng, $outbuf, $nRetOutLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC($outbuf, $nRetOutLeng);
Common::arraycopy_system($cdata, 0, $pbszCipherText, $i, $nRetOutLeng );
$i+= $nRetOutLeng;
}
$remainleng = $message_length%$process_blockLeng;
if($remainleng==0)
{
$remainleng = $process_blockLeng;
}
Common::arraycopy_system($planBytes, $i, $pbszPlainText, 0, $remainleng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszPlainText, $remainleng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $remainleng, $outbuf, $nRetOutLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC($outbuf, $nRetOutLeng);
Common::arraycopy_system($cdata, 0, $pbszCipherText, $i, $nRetOutLeng );
$i+= $nRetOutLeng;
KISA_SEED_CBC::SEED_CBC_Close( $info, $outbuf, 0, $nPaddingLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC($outbuf, $nPaddingLeng);
Common::arraycopy_system($cdata, 0, $pbszCipherText, $i, $nPaddingLeng );
$data = null;
$cdata = null;
$outbuf = null;
for($i=0;$i< sizeof($pbszCipherText);$i++) {
$ret .= sprintf(“%02X”, $pbszCipherText[$i]).”,”;
}
return substr($ret,0,strlen($ret)-1);
*/
}
function decrypt($bszIV, $bszUser_key, $str) {
$planBytes = explode(“,“,$str);
$keyBytes = explode(“,“,$bszUser_key);
$IVBytes = explode(“,“,$bszIV);
for($i = 0; $i < 16; $i++)
{
$keyBytes[$i] = hexdec($keyBytes[$i]);
$IVBytes[$i] = hexdec($IVBytes[$i]);
}
for ($i = 0; $i < count($planBytes); $i++) {
$planBytes[$i] = hexdec($planBytes[$i]);
}
if (count($planBytes) == 0) {
return $str;
}
$pdwRoundKey = array_pad(array(),32,0);
$bszPlainText = null;
// 방법 1
$bszPlainText = KISA_SEED_CBC::SEED_CBC_Decrypt($keyBytes, $IVBytes, $planBytes, 0, count($planBytes));
for($i=0;$i< sizeof($bszPlainText);$i++) {
$planBytresMessage .= sprintf(“%02X”, $bszPlainText[$i]).“,”;
}
return substr($planBytresMessage,0,strlen($planBytresMessage)-1);
/*
// 방법 2
$info = new KISA_SEED_INFO();
$nCipherTextLen = count($pbszCipherText);
$EncryptedMessage_length = count($planBytes);
if($EncryptedMessage_length%KISA_SEED_CBC::BLOCK_SIZE_SEED)
{
return “”;
}
KISA_SEED_CBC::SEED_CBC_init( $info, KISA_ENC_DEC::KISA_DECRYPT, $keyBytes, $IVBytes );
$process_blockLeng = 32;
$outbuf = array_pad(array(), $process_blockLeng/4, 0);
for($i = 0; $i < $EncryptedMessage_length-$process_blockLeng; )
{
Common::arraycopy_system($planBytes, $i, $pbszCipherText, 0, $process_blockLeng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszCipherText,$process_blockLeng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $process_blockLeng, $outbuf, $nRetOutLeng );
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC( $outbuf, $nRetOutLeng );
Common::arraycopy_system($cdata, 0, $pbszPlainText, $i, $nRetOutLeng );
$i+= $nRetOutLeng;
}
$remainleng = $EncryptedMessage_length%$process_blockLeng;
if($remainleng==0)
{
$remainleng = $process_blockLeng;
}
Common::arraycopy_system($planBytes, $i, $pbszCipherText, 0, $remainleng);
$data = KISA_SEED_CBC::chartoint32_for_SEED_CBC($pbszCipherText,$remainleng);
KISA_SEED_CBC::SEED_CBC_Process( $info, $data, $remainleng, $outbuf, $nRetOutLeng );
if(KISA_SEED_CBC::SEED_CBC_Close( $info, $outbuf, $nRetOutLeng, $nPaddingLeng))
{
$cdata = KISA_SEED_CBC::int32tochar_for_SEED_CBC( $outbuf, $remainleng-$nPaddingLeng );
Common::arraycopy_system($cdata, 0, $pbszPlainText, $i, $remainleng-$nPaddingLeng );
$message_length = $i+ $remainleng -$nPaddingLeng;
$result = array_pad(array(), $message_length, 0);
Common::arraycopy_system($pbszPlainText, 0, $result, 0, $message_length);
$data = null;
$cdata = null;
$outbuf = null;
for($i=0;$i< sizeof($result);$i++) {
$planBytresMessage .= sprintf(“%02X”, $result[$i]).”,”;
}
return substr($planBytresMessage,0,strlen($planBytresMessage)-1);
}
return “”;
*/
}
$enc = null;
$dec = null;
$textin = null;
$textout = null;
if(isset($_POST[‘ENC’]))
$enc = $_POST[‘ENC’];
if(isset($_POST[‘DEC’]))
$dec = $_POST[‘DEC’];
if(isset($_POST[‘TEXTIN’]))
$textin = $_POST[‘TEXTIN’];
if($textin<>null) { //평문문자열이 있으면, 이것으로 평문 HEX 구성
//HEX 변환
$enc = strToHexCommaSeparated($textin);
}
if($enc==null) {
$enc2 = “”;
} else {
//HEX 변환값으로 암호화 시작
$g_bszPlainText = $enc;
$enc2 = encrypt($g_bszIV, $g_bszUser_key, $g_bszPlainText);
}
if($dec==null) {
$dec2 = “”;
} else {
//복호화 시작
$g_bszChiperText = $dec;
$dec2 = decrypt($g_bszIV, $g_bszUser_key, $g_bszChiperText);
$textout = hexCommaToStr($dec2);//문자로 변환
}
//일반 문자열을 HEX 로 변환하고, 콤마로 분리하여 리턴
function strToHexCommaSeparated($string){
$hex=”;
for ($i=0; $i < strlen($string); $i++){
$hex .= ($hex ? “,”:“”) . dechex(ord($string[$i]));
}
return $hex;
}
//콤마로 분리되어 전달된 HEX 값에서 콤마를 제거하고 문자열로 변환하여 리턴
function hexCommaToStr($hexComma){
$hex = str_replace(“,”,““,$hexComma);
$string=”;
for ($i=0; $i < strlen($hex)-1; $i+=2){
$string .= chr(hexdec($hex[$i].$hex[$i+1]));
}
return $string;
}
?>
<html>
<head>
<meta http-equiv=“Content-Type” content=“text/html; charset=utf-8”>
<title>국산암호 [SEED – CBC] 테스트 페이지</title>
</head>
<body>
<center>
<h1>국산 암호 [SEED-CBC] 테스트 페이지</h1>
<form name=“myform“ method=“post” action=“./index.php“>
<input type=“hidden” name=“method” id=“method” />
<table border=“0”>
<tr>
<td style=“text-align:center;”>
<form method=“post” action=“./index.php“>
<table border=“0”>
<tr><td></td><td><암호화 예제></td></tr>
<tr>
<td>키(KEY) : </td>
<td><textarea name=“KEY” style=“width:400px;height:100px;”><?=$g_bszUser_key?></textarea></td>
</tr>
<tr>
<td>초기값(IV) : </td>
<td><textarea name=“IV” style=“width:400px;height:100px;”><?=$g_bszIV?></textarea></td>
</tr>
<tr>
<td>평문 문자열 : </td>
<td><textarea name=“TEXTIN” style=“width:400px;height:100px;”><?=$textin?></textarea></td>
</tr>
<tr>
<td>평문 HEX : </td>
<td><textarea name=“ENC” style=“width:400px;height:100px;”><?=$enc?></textarea></td>
</tr>
<tr>
<td></td>
<td><input type=“submit” name=“gogo“ value=“▼ 암호화“> </td>
</tr>
<tr>
<td>암호문 : </td>
<td><textarea name=“ENC2” style=“width:400px;height:100px;”><?=$enc2?></textarea></td>
</tr>
</table>
</form>
</td>
<td style=“width:1px;background-color:#aaaaff;”>
</td>
<td style=“text-align:center;”>
<form method=“post” action=“./index.php“>
<table border=“0”>
<tr><td></td><td><복호화 예제></td></tr>
<tr>
<td>키(KEY) : </td>
<td><textarea name=“KEY” style=“width:400px;height:100px;”><?=$g_bszUser_key?></textarea></td>
</tr>
<tr>
<td>초기값(IV) : </td>
<td><textarea name=“IV” style=“width:400px;height:100px;”><?=$g_bszIV?></textarea></td>
</tr>
<tr>
<td>암호문 : </td>
<td><textarea name=“DEC” style=“width:400px;height:100px;”><?=$dec?></textarea></td>
</tr>
<tr>
<td></td>
<td><input type=“submit” name=“gogo“ value=“▼ 복호화“></td>
</tr>
<tr>
<td>평문 HEX: </td>
<td><textarea name=“DEC2” style=“width:400px;height:100px;”><?=$dec2?></textarea></td>
</tr>
<tr>
<td>평문 TEXT: </td>
<td><textarea name=“TEXTOUT” style=“width:400px;height:100px;”><?=$textout?></textarea></td>
</tr>
</table>
</form>
</td>
</tr>
</table>
</form>
</td>
</tr>
</table>
<div style=“margin-top:20px;margin-bottom:20px;”><font color=“#ff0000”>※ 평문 문자열이 기록되면, 평문 HEX는 자동생성됩니다.</font></div>
<div style=“margin-top:20px;margin-bottom:20px;”><font color=“#ff0000”>※ 평문 및 암호문은 Hex 값의 0x를 제외하고 콤마로 구분하여 띄어쓰기 없이 입력합니다.(ex : 00,01,0A,0B)</font></div>
<div style=“border: 1px solid #aaaaff; background-color:#ddddff;”>
<table border=“0”>
<tr>
<td><키(KEY)> : </td>
<td>88,E3,4F,8F,08,17,79,F1,E9,F3,94,37,0A,D4,05,89</td>
</tr>
<tr>
<td><초기값(IV)> : </td>
<td>26,8D,66,A7,35,A8,1A,81,6F,BA,D9,FA,36,16,25,01</td>
</tr>
<tr>
<td><평문> : </td>
<td>00,01,02,03,04,05,06,07,08,09,0A,0B,0C,0D,0E,0F</td>
</tr>
<tr>
<td><암호문> : </td>
<td>75,DD,A4,B0,65,FF,86,42,7D,44,8C,54,03,D3,5A,07,D3,5A,AB,86,7C,8B,F2,55,7D,82,38,8E,A7,C0,D0,F1</td>
</tr>
</table>
</div>
</form>
</center>
</body>
</html>
